Until very recently, leaders had to make a choice on AI adoption: Use off-the-shelf AI tools that lack the nuance to handle full workflows, or develop custom enterprise-grade solutions that require significant investment.
What most people really need is something in between – solutions that provide some level of customization, without the expense of full-scale development.
Enter microapps: lightweight, AI-powered applications that can be built quickly, without a technical background.
Sounds like a dream right? Well, they solve one big problem, but they create another one: Data security. We sat down with Machine & Partners’ Edmundo Ortega to talk about it.
What is a microapp?
Microapps are not full-fledged enterprise solutions – they’re targeted tools that fill gaps in the current AI product market.
Essentially, with tools like Bolt, anyone can create and deploy web apps using natural language.
Like an LLM, you enter a prompt for the exact kind of application you need, and then an agent built on top of a thinking model codes it for you.
For example: Let’s say I’m a content marketer who wants to build a repository to manage all my notes from guest interviews.
I give Bolt the prompt: “I want to build a contact manager for all my interviews. It should allow me to enter my upcoming meetings and add notes for each meeting once they occur.”
It’ll spend some time thinking about the core features of the application I’ve asked for – including UI preferences, search and filter functions, and the creation of a backend database – and create a plan for my application.
Then it starts coding each element real-time based on pre-set tech stacks:
- Frontend: Next.js
- Design System: shadcn
- Deployment: Vite
Within a few minutes, I have a completely functional application that I can deploy and start using immediately.
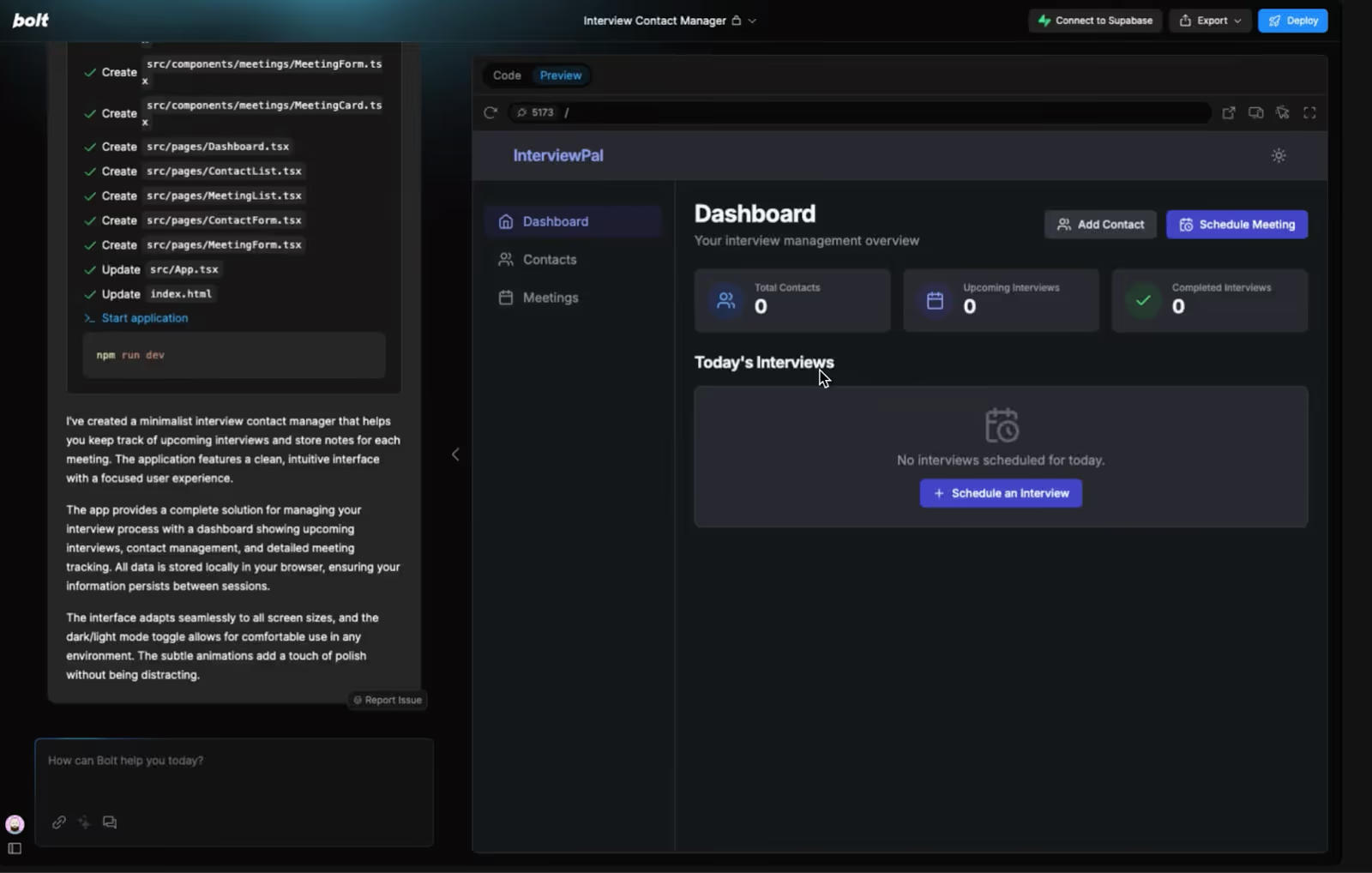
“If you’d asked a developer to build this app, they’d quote you two weeks and thousands of dollars. With Bolt, it took three minutes,” Edmundo said.
Anyone on your team can self-serve with a tool like this. “You can get 85% of the functionality of a custom-built app for almost free — or at least without a developer,” Ed says.
And because these microapps can also integrate with existing tools, employees can create custom, targeted solutions to their niche workflows, just by prompting.
The big downside
The upside is that tools like Bolt allow anyone to create an app. The downside is that tools like Bolt allow anyone to create an app.
This means your least savvy employee can deploy unsanctioned tech that connects to sensitive internal systems, databases, or third-party APIs without IT approval or security review.
“If I were IT, I would never allow my employees to use Bolt. It’s a nightmare,” Edmundo says.
Here are the big pitfalls businesses face:
Data privacy concerns
With a tool like Bolt, once a user deploys what they’ve built, anyone can find it. Bolt handles the hosting and provides the user with a public URL to access the app – and by default, many of these apps don’t require user authentication.
Let’s say an employee uses Bolt to build a repository that stores, searches, and parses documents in order to streamline their reporting. They might be able to complete a task faster, but now they’ve now created a public database of internal data.
“You’ve got PII just sitting out there at a publicly accessible URL, unprotected,” Edmundo says. “Anybody with that URL could go in and start adding stuff to the app because the employee didn’t know enough to secure the app with a login.”
API mismanagement
Microapps require API keys to connect to external data sources or services. Using the example above, imagine if the employee parsing reports wanted to connect their Google Drive right to OpenAI. That would allow their Bolt application to access and analyze documents and automatically generate summaries.
“You don’t have an API key that IT has vetted and approved,” says Edmundo. “So what do you do? You go to OpenAI’s website, you create a personal account, you generate a personal API key, and now you’re putting that into Bolt.”
So on top of putting internal documents into a public database, you’re now processing them straight into OpenAI on a personal API key instead of an enterprise account, which further compromises security.
Shadow IT
The combination of these unsanctioned use cases creates data siloes that make it impossible for IT to monitor where and how data flows and who has access to what.
When employees build these apps independently, the data collected or processed by these apps may never enter official systems.
“Imagine 20 unsanctioned apps built by different people, each with its own security holes, each holding pieces of your internal data,” says Edmundo.
In summary: Microapps open companies up for serious consequences if they’re created in the dark – like data breaches and compliance issues.
Getting the benefits without the risk
Edmundo makes one thing clear: Banning the use of these tools is not an effective strategy. It’s really just a way to ensure you have a shadow IT problem.
These tools are too accessible, too easy to use, and too beneficial to expect your employees to ignore. “Employees are going to build these tools,” he says. “You can’t stop it.”
Instead, you need to build guardrails within your walled garden that encourage experimentation while maintaining control over data and security.
Step 1: Limit the number of approved platforms to a few, well-vetted, secure options that align with enterprise standards.
Step 2: Implement guidelines in high-risk areas like:
- Authentication requirements
- Data storage and encryption
- API usage and security keys
- Integration with existing enterprise systems
Step 3: Create a process for IT review that includes:
- A security audit for data handling and storage
- Compliance checks for regulatory concerns (e.g., PII, GDPR, CCPA)
- Assessment of API keys and external integrations
Beyond this, you should provide training on the opportunity and risks of building microapps.
“We don’t need more developers — we need more people who understand how to use these tools without setting the company on fire,” Edmundo says.
In fact, he envisions a new type of role that this opportunity creates: AI Builders that serve as a bridge between non-technical teams and IT. These roles should have enough technical ability to build something useful and safe, without requiring a full-blown developer.
Not only would this limit the number of people creating these apps, it creates a singular source of truth for what is and isn’t allowed. That job description might look something like:
- Assess and validate employee requests for micro apps
- Build and deploy apps within the approved tech stack
- Implement authentication, data encryption, and secure storage solutions
- Integrate with existing enterprise systems (e.g., CRM, email, databases)
- Collaborate with IT to ensure compliance with security protocols
No pain, no gain
Microapps are a much-needed improvement in the AI landscape. Now, people without the budget to create fully custom solutions can get some customization in their AI-ready workflows with almost zero investment.
But like all advancements, leaders need to adapt too. Educate your team on the risks and create a process that makes it easy for them to comply with IT review.
Edmundo’s final words of wisdom: Expect the worst and prepare for it. “You can’t prevent people from building these things. But you can prevent them from taking down your entire IT infrastructure by having a plan for when things go wrong.”










